This article’s indented audience is people who want to regain some digital privacy but haven’t heard much on the topic before.
There are five effective first steps that can be taken by freedom-seekers to dramatically increase the amount of privacy in their lives. Those steps are:
- Use an encrypted messenger (such as “Signal” by Open Whisper Systems)
- Use a privacy respecting search engine (such as startpage.com or duckduckgo.com)
- Use a web-browser that respects your privacy
- Totally stop using voice-based personal assistants (such as Alexa, Google Assistant, Siri, Cortana, etc)
- Harden the permissions on your mobile device (This one is the hardest to do, but it is the MOST rewarding)
Use an Encrypted Messenger
Right now, all your Facebook messages, all your Google chats, and all your text messages aren’t private. The folks at Facebook and Google almost certainly analyze all your personal messages with robots designed to learn everything they can about you, and your mobile carrier may very well be doing the same with your text messages and phone conversation metadata. In our world, it is imperative that everyone who believes in privacy utilize tools that make this sort of exploitation impossible. In this case, our tool is end to end encryption. We highly recommend you do your own research on this so you understand its significance, but essentially it uses cryptography (cryptography is a branch of applied mathematics) to scramble messages in a way where there is no known way to unscramble the messages unless you have the secret mathematical key (which only the intended recipient should have). In layman’s terms, it makes it extremely difficult for someone to see your messages. Instead of just listening “on the wire” and getting your messages, they would have to hack you, which is significantly harder, more costly, and more time consuming. At present time, the app “Signal” by Open Whisper Systems is the largest adopted open-source end-to-end encrypted messenger available on both the Apple App Store and Google Play Store. This app does all the heavy lifting for you, the only thing you have to do is convince your peers to download it too as you can only communicate with end-to-end encryption with someone else who also has the app. Signal also supports end-to-end encrypted phone and video calls. We have found it extremely easy to convince a large number of the people we know into getting Signal because it is so easy to download and set up.
Use a Privacy-Respecting Search Engine
Right now, whenever you search something on Google, your search query, the location you searched it from, the time you searched it, as well as the browser and computer you searched it from are all associated with your identity. Over time, as you search more and more and click on the associated search results, conclusions such as your habits, destinations you frequent, major life events, and even your political opinions can be derived from this data. We know for a fact that Google actively derives as much data from you as they can, but there are certain search engines that at least promise they throw collected data away and don’t attempt to infringe on your privacy as you use their services. Check out Duck Duck Go and Startpage and follow their instructions for switching your default search engine over to them in order to make your internet searching more private. Due to this strategy depending on the good faith of the aforementioned companies, this option unfortunately does not “enforce your freedom” as our motto here at Crypto-Armory goes. In a future privacy-oriented blog post, we will show you exactly how you can enforce your own privacy on the web – it’s just a bit too in-depth for this blog post, but if you are curious, you can read more about how Tor can enforce your privacy on the web at the following link: https://torproject.org/
Use a Web-Browser that Respects Your Privacy
Google Chrome seems to be the most popular web browser. Not only is it closed source, but it is known to collect telemetry data (information about your device, browsing habits, etc) and send it to Google. Firefox is an open-source browser that does not do this. Even better, Brave is a web browser that not only is open source and doesn’t log invasive telemetry data, but also blocks online trackers and advertisements by default. We recommend checking them out. For the most private browsing experience, use the Tor browser, although some websites will not let you view them with TOR. We hope to talk more about Tor in a future blog post.
Totally Stop Using Voice-Based Personal Assistants
Totally stop using assistants such as Alexa, Siri, Google Assistant (such as “Google Home”), Cortana, etc. There’s really not much else to say about this, just stop using them. Because of the closed-source, cloud-based nature of these products, there is no way to validate whether or not they listen to you and log what you say when you aren’t using them. Until an open source alternative is identified, totally avoid these products.
Harden the Permissions on Your Mobile Device
Ever mentioned a product while talking to a friend, and later seen ads for it? One of the apps on your phone likely has permission to your microphone and is listening to everything you say. Applications you install on your phone will likely take advantage to every permission you give them. They’ll use your GPS to track you, your camera to watch you, your contacts list to track the people you associate with, pictures on your phone to gauge your interest, as well as other things in an attempt to learn all they can about you so they can sell your data to advertising agencies or anyone who will pay. Fortunately for you, this exploitation can be mitigated by managing the permissions on your phone, meaning you can prevent apps from accessing your microphone, location, camera, etc. Certain apps will still need specific permissions to function as intended – for example, calls will not work if the phone app doesn’t have access to your microphone.
The way you change app permissions is different on each phone and you may have to do some digging to find the appropriate settings screen. Hardening permissions on your mobile device is definitely one of the least straightforward steps to regaining digital privacy, but it is certainly one of the most important.
On my android device, I open settings, then tap “Apps & notifications”, then “Advanced”, then “App permissions”. From here I see a category of each permission type and the number of apps that request that permission, as well as the number of apps currently given that permission. See the below screenshot taken from my Android device.
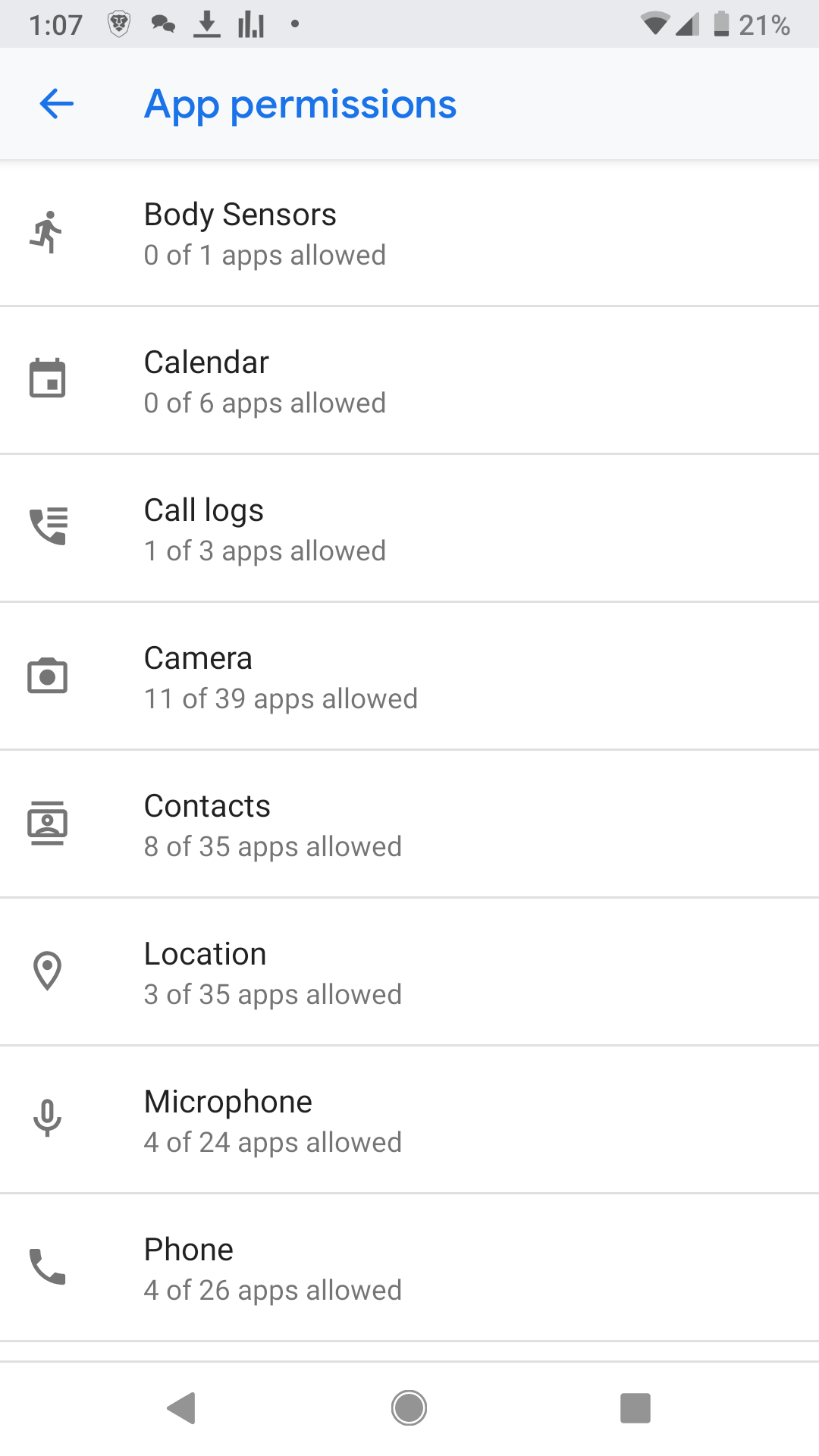
I can tap a permission and then manage which apps can have that permission. See the below screenshot.
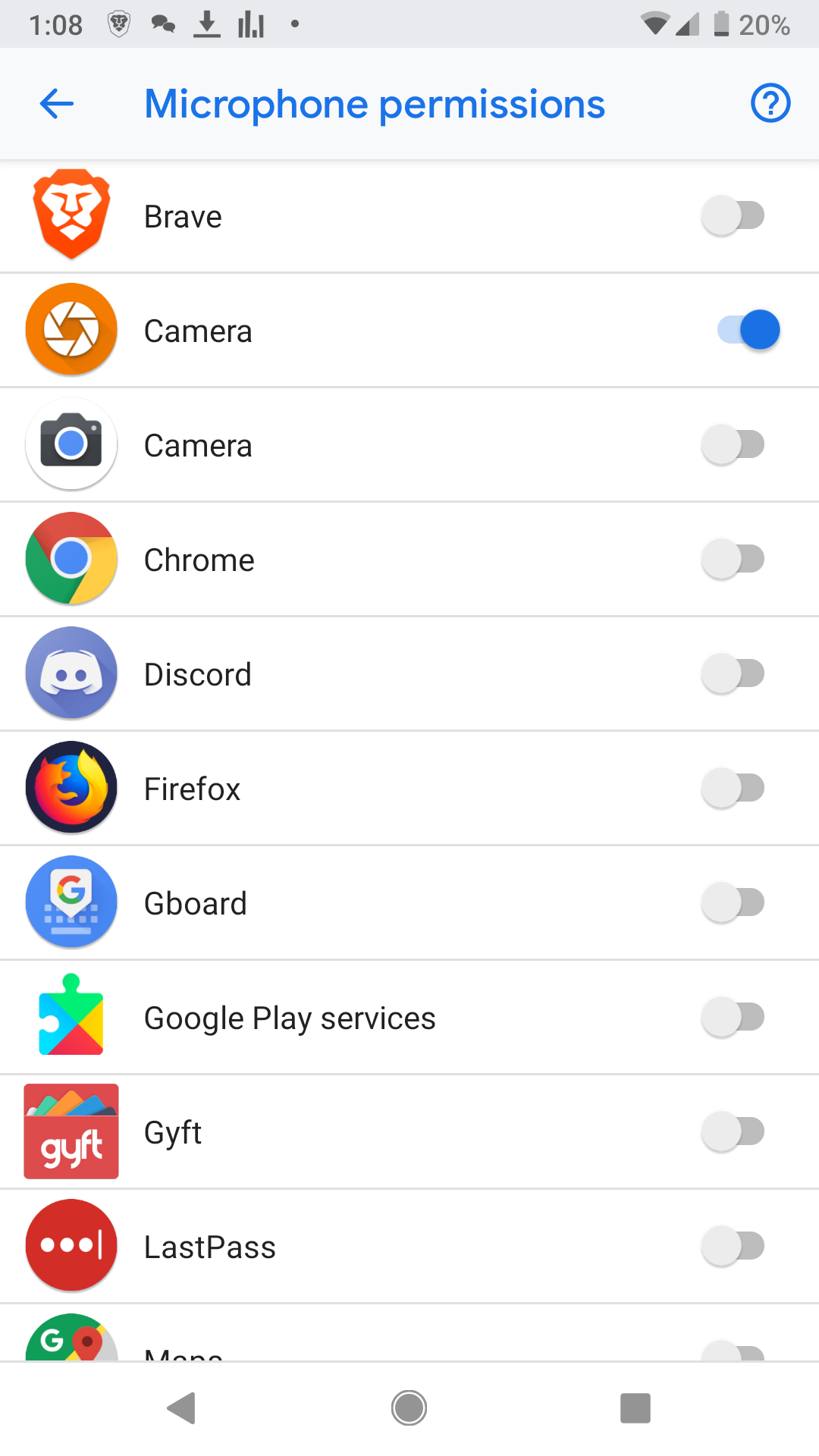
Don’t just deny all permissions, again, some apps clearly need certain permissions to function. Your camera app needs access to the camera permission in order to take pictures. Your camera app usually also needs access to your microphone so it can take videos. However, your camera app DOES NOT need access to your contacts. Why would it? Also, your camera app will also need access to your storage so that it can save the pictures you take.
The rule of thumb here is apps should have the least amount of permissions necessary to serve you. This is generally called the rule of “least permissions” in information security.
Please note that apps might stop working the way they are suppose to if you deny the permissions they ask for, you’ll probably have to fiddle around with it.
Some links for further reading on this topic are below:
A guide for managing Android permissions can be found here: https://www.howtogeek.com/230683/how-to-manage-app-permissions-on-android-6.0/
A guide for managing iPhone permissions can be found here: https://www.howtogeek.com/211623/how-to-manage-app-permissions-on-your-iphone-or-ipad/
